....continued from the previous blog – Functions of Corporate Digital Responsibility.
CDR and Data Security

This might be one of the most misused term of the recent decade. Anything and everything that is categorised as data ends up coping with digital security one way or the other. Every corporation follows their own internally drafted policies or some externally defined certifications on data security and even implement some good firewall security, DLP software, end point security software and many more in order to thwart any unprecedented attempt of stealing data. But yet the thefts continue to happen, even in the most reputed corporations with the most advanced technology.
The most recent one being that of ebay where the hack put millions at risk of identity theft. It was very brave of ebay to accept the incident openly and advise all its 145 million active users to change their passwords immediately and I was one among. The accounts were suspended temporarily in order to ensure that the data on the ebay platform would not be compromised. This has been the case with most of the reputed organisations after a customer sued Amazon after the hackers attack. As published in Bloomberg news on the 18th of Jan, 2012 ‘Amazon.com Inc. (AMZN) was accused in a lawsuit by a customer of its Zappos.com unit of violating federal consumer credit laws by failing to protect her personal information after the company said hackers stole account numbers and other data’. It was therefore a lesson to all the corporations to come out openly accept that a hack has happened and recommend all its users to change the password immediately and suspend their accounts till they do so.
Let’s now look at the other side effects of a hack. For instance the hacker has already retrieved the credit card and all the other personal and financial information about the individual stored in the user account even before the company gets to know about the hack. What is the benefit of suspending the accounts post that? This is what we call closing the gates of the fort after the king was captured, what is the point when the battle is already lost. Is this a mere eyewash posing as though they are doing their best. To an extent it is and what else would you expect from the corporation. The people running the corporation are individuals too, the people writing the antivirus are people too and the people writing virus are people too. What it means is, as per the theory of evolution where the life started with a tiny molecule and has been evolving since then, similarly science and technology has evolved too. No matter what technology one adopts to secure the data, there are people whose fulltime work is to break them and most of them succeed. It is therefore a game of a Cop and the Crook. According to recent survey by CNET, ‘Vast majority of hackers believe they are above the Law’. What would you expect about the data security in such a mindset of individuals working round the clock in a destructive manner just for fun.
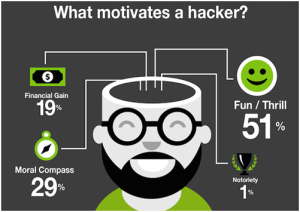
Adopting a new technology for data security is the solution only for a particular time frame until it is either evaded or an updated/upgraded technology is available. Whatever the technology, the data threat will always prevail. The other side effect of a data theft apart from losing data from the account is the password itself. A survey conducted by ZDNet in 2011 suggested that more than 60% of the individuals use the same password across multiple accounts. In such a case, imagine the kind of threat that an user can get into if one of their accounts gets hacked. The results can be catastrophic from a mere financial gain to a terrorist intent. It is therefore logical to think that the data can never be secure and all that one can do is do their best to secure it for the time being.
Source: CNET
Apart from the local government regulations that identifies data security as a critical component of good governance in corporations, there are also the certifications from the international standards organisations such as the ISO/IEC 27001 and the ISMS. All the standards and regulations emphasizes the need of apt data security at the work place. In order to get certified under these standards, the organisation will have to identify and implement practices that will educate their employees about data security and its significance to the company and implement practices and technologies that will protect data. An important point to nice is that the opting for the certification is optional and is something that the organisation decides to go with and not mandatory. Most of the organisations who get themselves certified under these standards are doing so in order to satisfy the requirements of either a RFP or a to satisfy a big client/prospect whose norms are to work with ISO certified client and vendors only.
From a CDR’s standpoint, it is very important that the organisation understands the nuances of data security and makes it a standard practice to record the activities and initiatives that the organisation has implemented around the data security. If the corporation and its employees are responsible for the safe keeping of the data, the customers are responsible for helping the corporation’s cause in indulging in activities such as changing their passwords frequently and so with the other associates of the corporation. It is therefore necessary to define a policy driven practice to educate all the associates to share the responsibility equally. It is very important that the organisation educates both their internal customers and their external customers on the data security obligations with either regular newsletters or emails or even social interactions on social media platforms and makes it a periodical practice that goes on continuously.
Recommended activities under ‘Data Security’
- Define data security practices for both the internal and external customers alike.
- Come up with a time driven periodical and automated process that will initiate a relook at the processes and infrastructure on the data security front. For example, resetting of the password for all data accesses and evaluating the security infrastructure with real time, real like security audits.
- Be open to technological updates in the market on the data security front.
- Be vocal with all the stake holders, both internal and external on the initiatives that the corporation has taken on securing the data.
- Educate all the stake holders on the pros and cons of data security and the different forms and areas of data threats.
- Understand and make people understand the facts about the data never being secure but the corporation can only do its best to secure the data at hand.
We need to understand that it is not necessary to indulge in mentioning the kind of technology the organisation uses to secure their data, it would be too foolish to do so. By exposing the kind of technology, the corporation would be inviting trouble by telling the hackers on what to expect, nobody does this actually. As for the ISO/IEC 27001, ISMS is concerned, this International Standard specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organization and implemented mostly within the organisation. The actuals of the actions taken and the audit report is never made public and only the certification matters. In case a client needs to know as what are the steps taken to secure their data, only then will the corporation reveal the information, that too with a signed NDA (Non-Disclosure Agreement) in place.
What we are proposing through CDR is something similar but much beyond that. A corporation has to not only implement the security standards internally but also has to demonstrate their intent with all the concerned by being vocal in the outside world. It is important for a corporation to have all its associates to be on the same page and thus exhibit the responsibility of owning and securing the data that originally belongs to its associates. That’s why it is called ‘Corporate Digital Responsibility’.
to be continued....